Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.
You can probably imagine why it might be useful to find out if a business is real or not. It can also be helpful to verify if a particular person works for a company they say that they do. While this information almost always exists, it's not usually accessible with a simple Google search. A lot of this information is in databases that require you to submit search queries to discover it.
Background Check a Business
To be a good researcher, we'll have to find out where the information is, and what search terms we'll need to use to extract it. Whether we're doing recon on a business to find out if it's legit, or looking for a target to craft the perfect phishing email to, there are plenty of reasons why this information might be useful.
If you want to know that a business is legit, the best place to start is digging into their licenses and key people. Finding evidence of being licensed is a positive sign, and will also lead to the names of the employees and officers listed on those documents. Finding these official documents allows you to cross-check information to look for inconsistencies or patterns, like the same people or addresses being used to register similarly disconnected businesses.
Create the Perfect Phishing Email
If you're a penetration tester, business research can take a more offensive turn by looking for the people, documents, and opportunities needed to craft the perfect phishing email. Getting a high-level executive to do something they're not supposed to do, like open a PDF from a stranger, can be done if the file is one the hacker knows their target is expecting.
If we wanted to send a malicious PDF to someone who will open it at a company, we need to know a few things first. First, we need to identify the people who deal with the paperwork, and others they speak to to do their job. We also need to know that the document they're expecting to see looks like, preferably by first locating a scanned version online.
With the right information, we can craft a phishing email to the right employee that looks like a document they're expecting to see from someone they trust. By digging, we can even add in the signatures of other executives, to make our PDF even more convincing.
Let's take a look at what we can dig up.
What You'll Need
To follow this guide, you'll only need an internet connection and browser. The great thing about OSINT is that we don't need many resources to do it, and we can often rely on clever search terms or a well-framed original question to extract the information we need.
Step 1: IntelTecniques Business Tools
To get started, navigate to the IntelTechniques website, and click on the "Business" menu to show the "Business resources" option. Click on this to navigate to the business resources page.
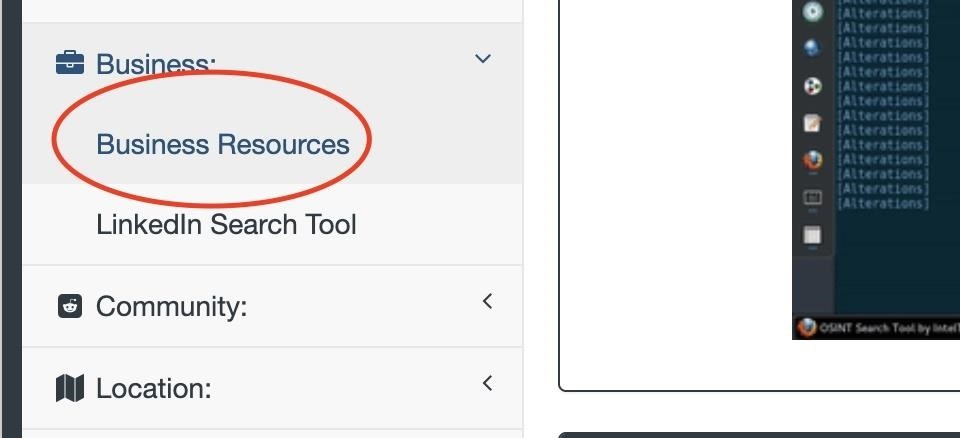
Here, we'll find a number of valuable tools for locating information about businesses. We'll use this page as a reference for links, and come back to it later.
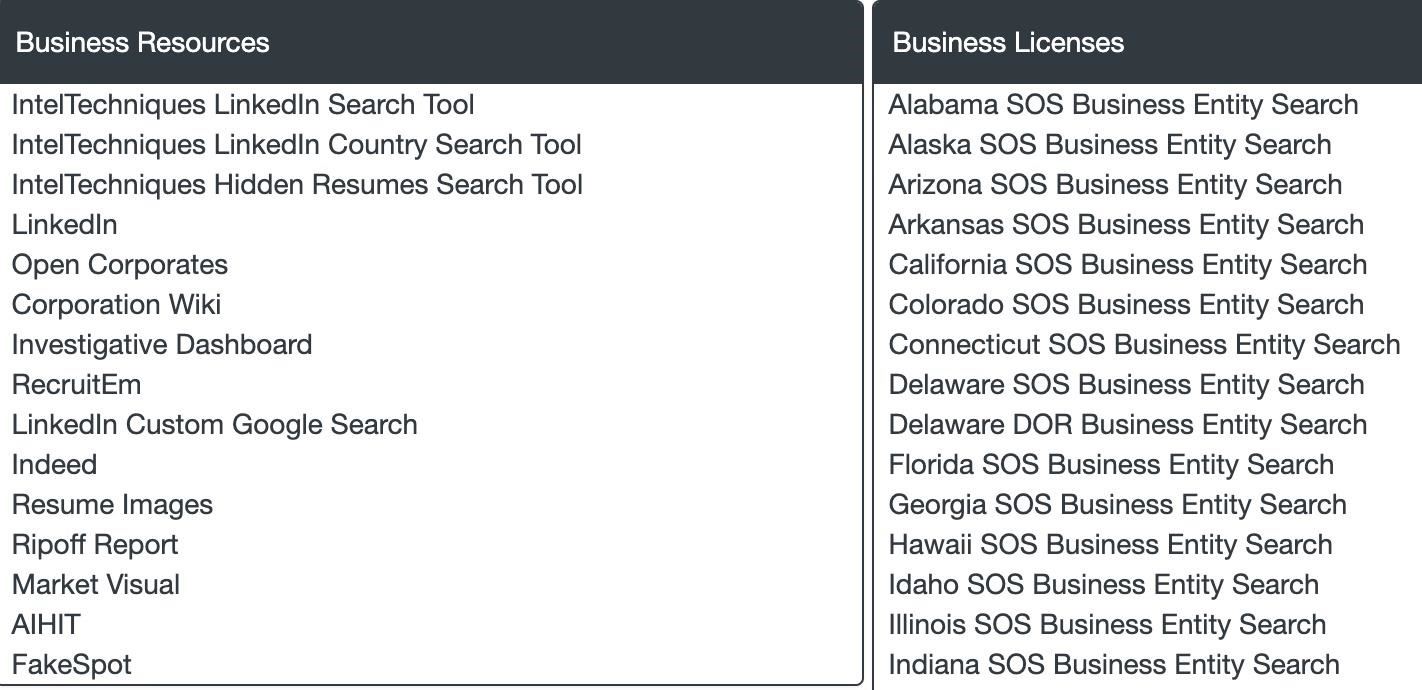
To start, you'll notice the list of secretary of state business search websites for every state. These links are where we'll start our search.
Step 2: Select a Target & Search State Databases
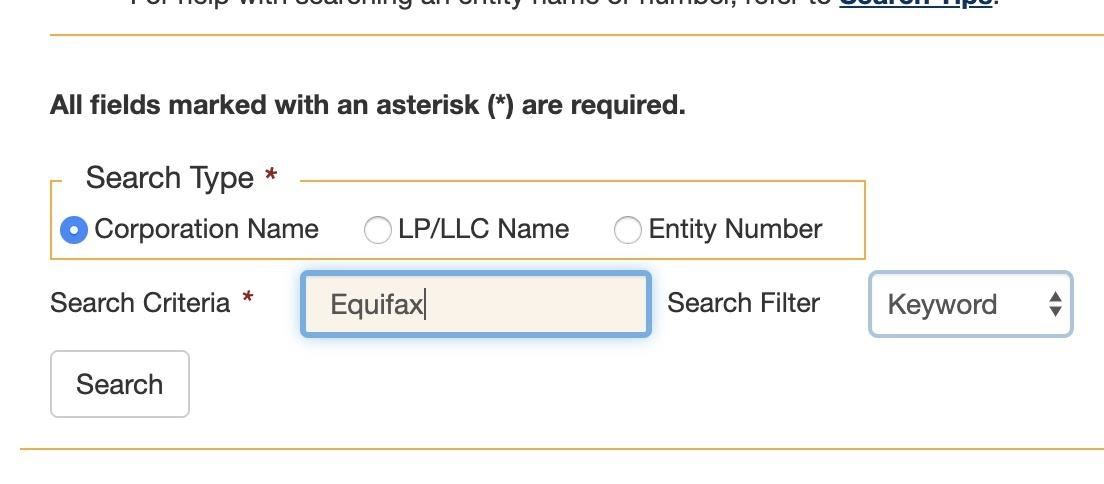
Our target today will be Equifax. We'll start by trying to identify the state in which they do business. Because the state of California is enormous and requires a lot of paperwork to do business in, it's a safe bet that if the business you're looking for is large, they do business and have paperwork filed there.
Navigate to the California Secretary of State Business Search page, which will allow you to search for documents from any company doing business in the state of California. Type in your search term, and select a corporation for larger companies, and an LLC for smaller ones. If you don't get a result the first time, rerun the search with the other option.
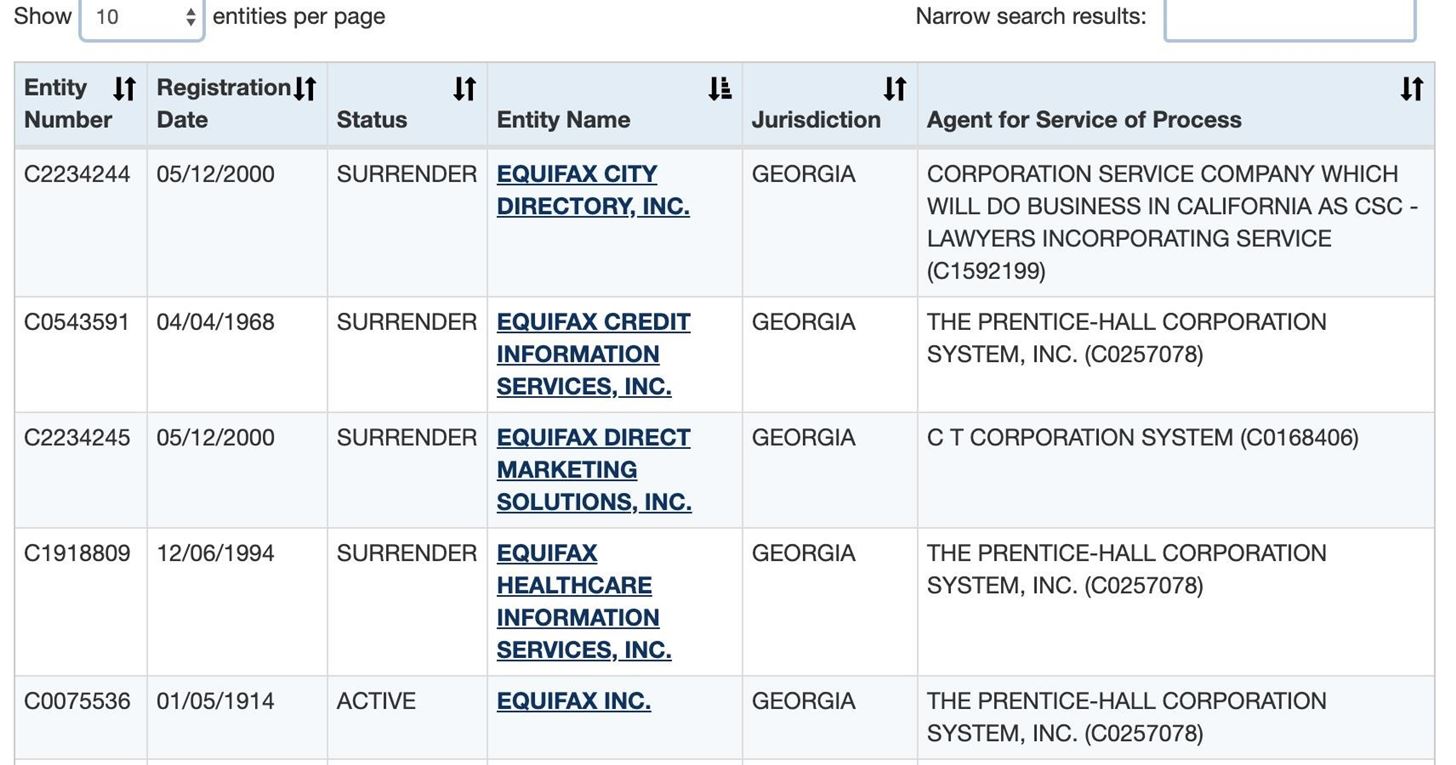
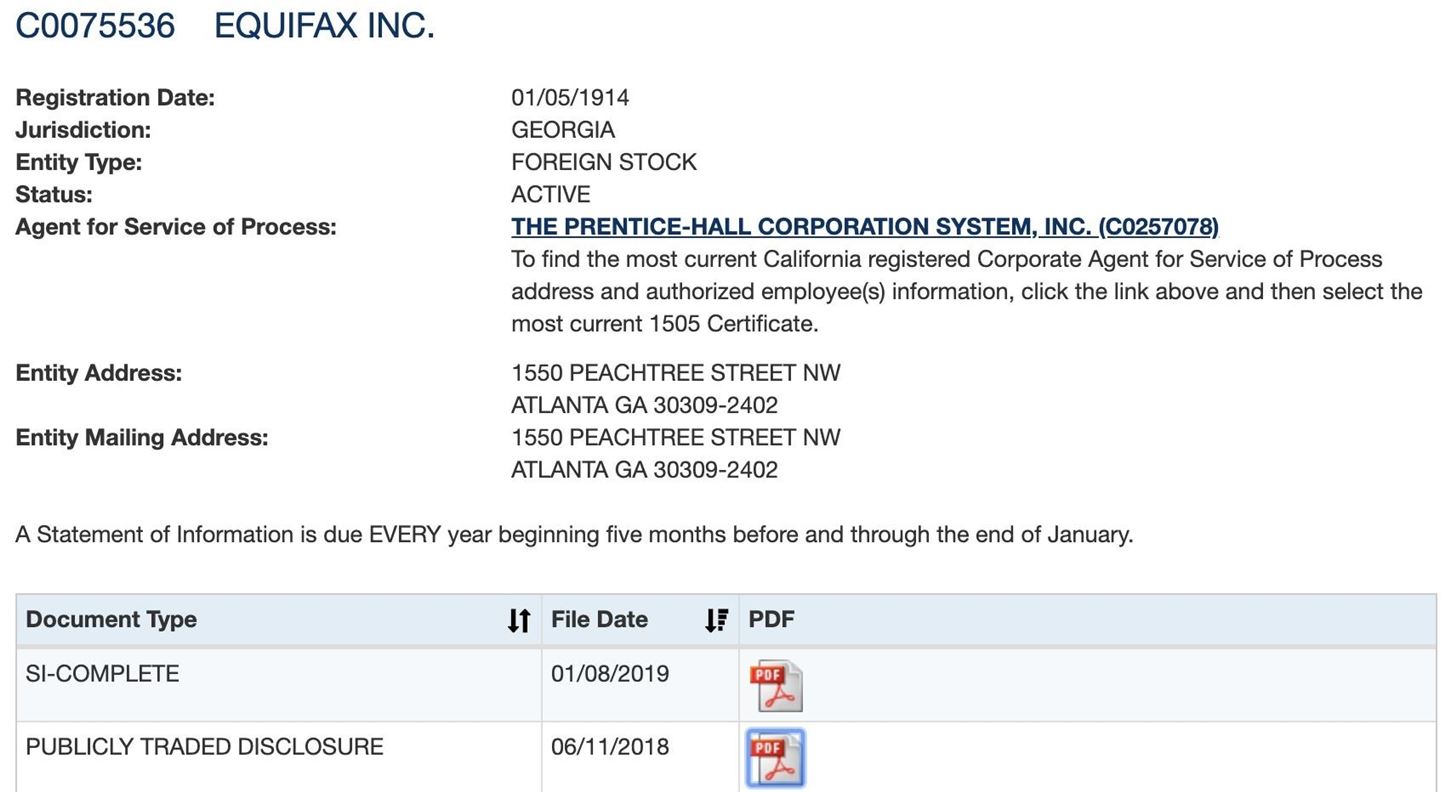
The results should link to business documents, and here we can see there is only one active listing for Equifax. We now know what state we can find more information in, Georgia.
Clicking on the active listing, we can see information on the filing, including an exact address. We can also see PDF files of documents they have submitted.
Step 3: Find Signatures in Documents
To start finding signatures, we can take a look at the documents we've located. The second document we find listed contains not only a signature, but also the name of everyone important in the company.
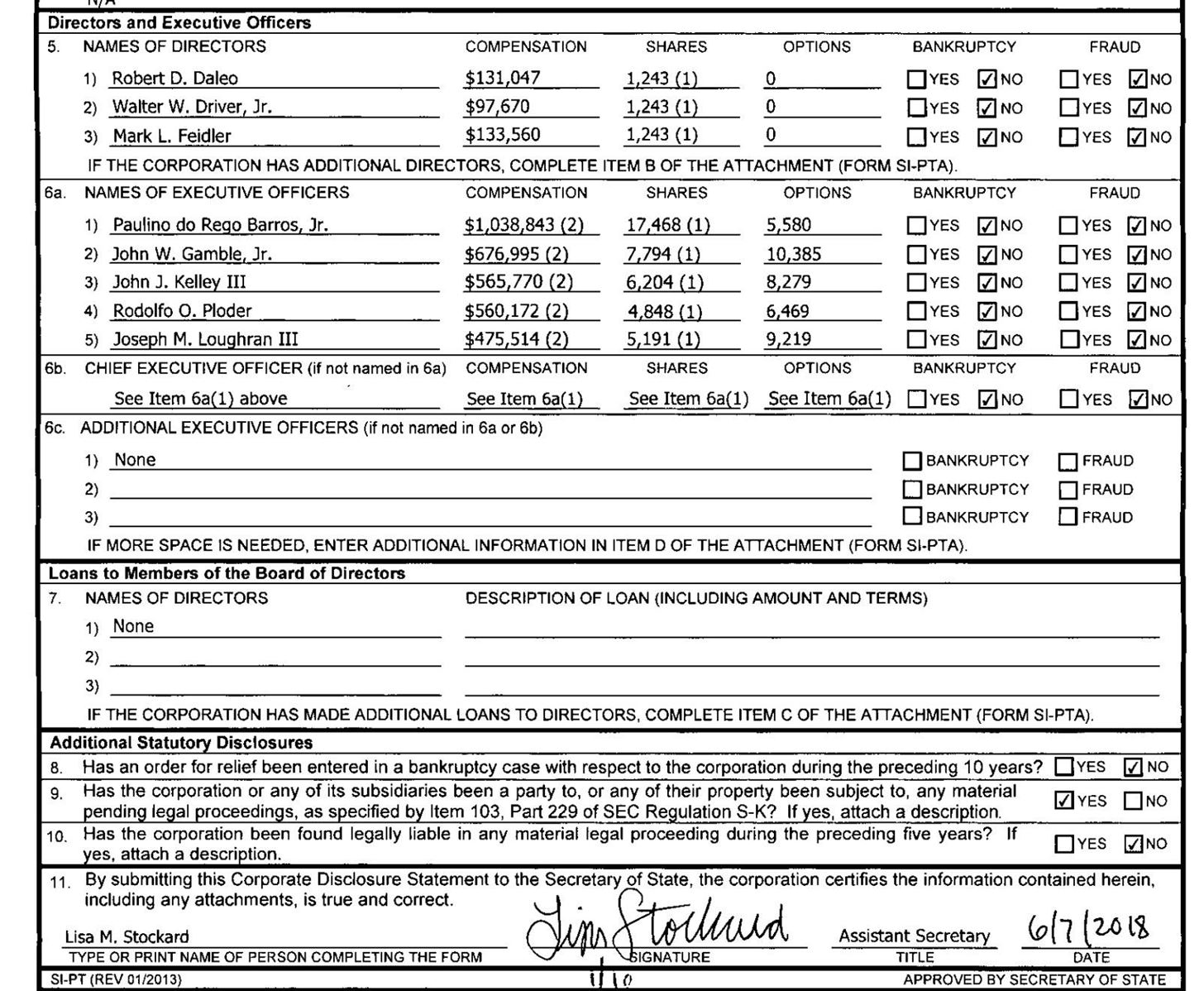
We already have several of our goals accomplished now that we know who does the paperwork, but we still need to know who to pose as and to what email address to send it. For that, we'll turn to another data source.
Step 4: Opencorporates.com Search
Back on the IntelTechniques page, we'll click on the link to OpenCorporates.com. This site allows us to search through company documents not just in one state, but in all states at the same time. While this may seem useful, it can quickly become overwhelming if we don't know where to search first.
Searching for "Equifax" turns up over 700 results! To reduce this, we can check "exclude inactive" to remove listings from businesses that are no longer active, which reduces the number to 373. But if we filter to only include businesses in Georgia, we're down to only 21.

Within this list of 21 businesses, a business called the Equifax foundation looks interesting. If we click on it, we see the same employee's name that we saw before on the company's information. We can also click on the employee name and run a search through LittleSis.org to find more documents that mention them.
The same name, plus the same address as the other filings, means this business is connected to the main Equifax business. At the bottom, we can see a link to a registry page in Georgia.
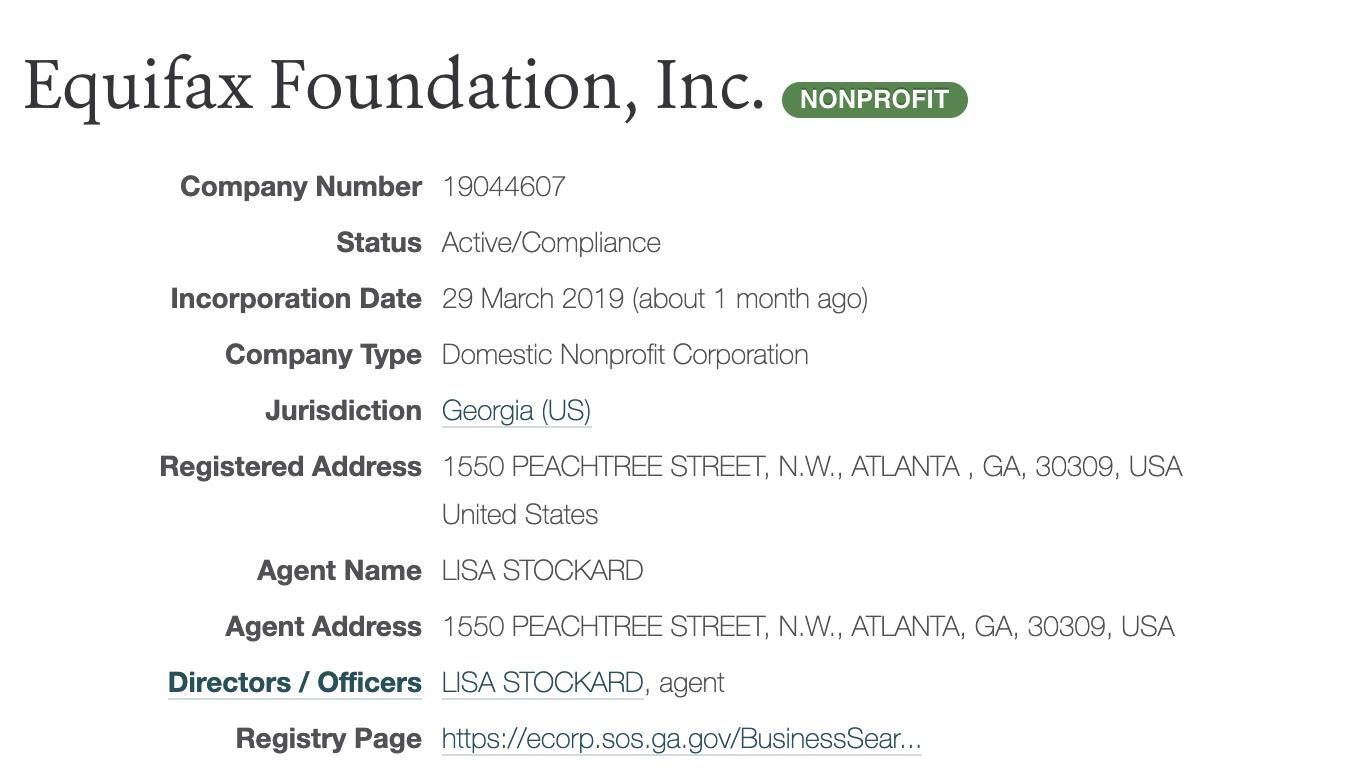
If we follow the link, we can see an entry for this business entity that also has a link to the filing history. This link leads to scanned documents that were used to create this business reasonably recently.
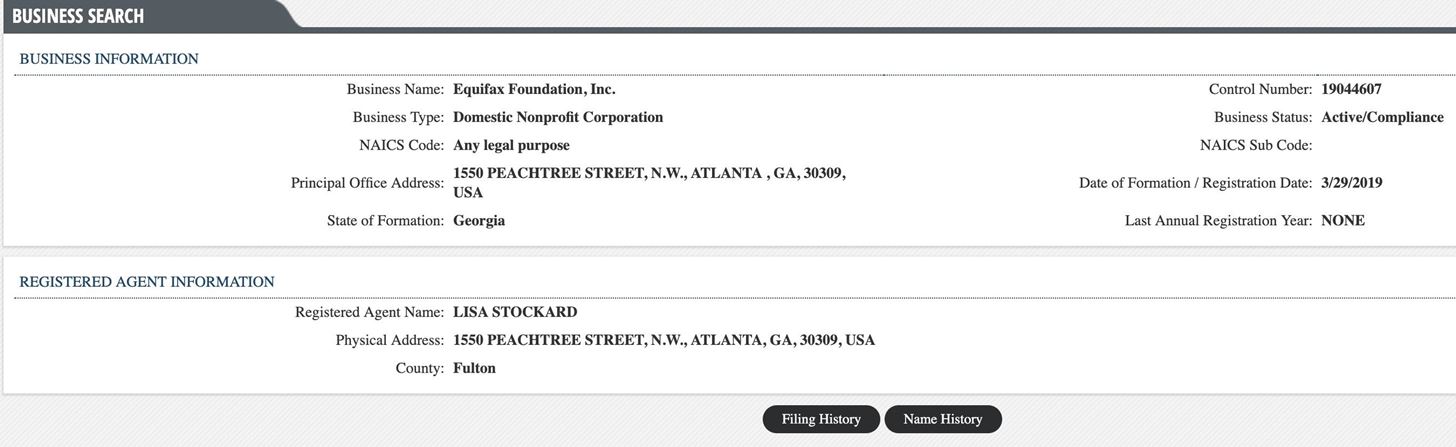
Finally, we get what we're looking for! In the only document uploaded with this entry, we get an email address, name, and other information about the people responsible for the paperwork. We now know the email addresses and phone numbers of both people who need to contact each other about filing state paperwork, and we have enough information to craft a reasonably targeted phishing email.

These details should be enough to phish some high-level employees. If we need to dig further, there's another tool we can use to dig deeper into the people behind the business.
Businesses Are an Easy Target for OSINT Research
Unlike individuals that may have some expectation of privacy, businesses generate paperwork with nearly everything they do. This makes researching them a breeze for hackers or anyone who needs to verify a business or executive, provided you look in the right database. You should be aware of what information is out there about any business you work with before opening a suspicious email at work, especially if it contains an attachment like a PDF.
I hope you enjoyed this guide to using OSINT techniques to research businesses! If you have any questions about this tutorial on business research, leave a comment below, and feel free to reach me on Twitter @KodyKinzie.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















1 Comment
Hey Kody. You will find this little trick can work sometimes... dorking. A lot of times just dorking for filetype:pdf can reveal signatures since PDF makes it easier to share and pass around files which usually get uploaded to third party for some odd reason. ;)
Share Your Thoughts